Secret管理 原创
1、功能

2、类型转换
2.1、实现类型转换
在 internal/pkg/k8s/secret/common.go 文件中新增 SecretCell,实现和 corev1.SecretCell 进行类型转换,如下:
package secret
import (
corev1 "k8s.io/api/core/v1"
"time"
"github.com/joker-bai/hawkeye/internal/pkg/k8s/dataselect"
)
type SecretCell corev1.Secret
func (p SecretCell) GetCreation() time.Time {
return p.CreationTimestamp.Time
}
func (p SecretCell) GetName() string {
return p.Name
}
// toCells batchv1.Secret 类型 转换成 DataCell 类型
// @description: Secret类型转换成DataCell
func toCells(sts []corev1.Secret) []dataselect.DataCell {
cells := make([]dataselect.DataCell, len(sts))
for i := range sts {
cells[i] = SecretCell(sts[i])
}
return cells
}
// fromCells DataCell 类型转换成 batchv1.Secret 类型
// @description: DataCell类型转换成Secret
func fromCells(cells []dataselect.DataCell) []corev1.Secret {
ds := make([]corev1.Secret, len(cells))
for i := range cells {
ds[i] = corev1.Secret(cells[i].(SecretCell))
}
return ds
}2.2、实现增删改查
(1)创建 internal/pkg/k8s/secret/create.go 文件,输入以下内容,用于创建 secret
package secret
import (
"context"
"encoding/base64"
"encoding/json"
"fmt"
"github.com/joker-bai/hawkeye/global"
"github.com/joker-bai/hawkeye/internal/app/requests"
"github.com/joker-bai/hawkeye/internal/pkg/k8s/common"
corev1 "k8s.io/api/core/v1"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
)
const (
DescriptionAnnotationKey = "description"
)
type DockerConfig struct {
Auths map[string]AuthEntry `json:"auths"`
}
type AuthEntry struct {
Username string `json:"username"`
Password string `json:"password"`
Auth string `json:"auth"`
}
func CreateSecret(ing *requests.K8sSecretCreateRequest) error {
annotations := map[string]string{}
if ing.Description != nil {
annotations[DescriptionAnnotationKey] = *ing.Description
}
labels := common.GetLabelsMap(ing.Labels)
metadata := metav1.ObjectMeta{
Annotations: annotations,
Labels: labels,
Name: ing.Name,
}
serv := &corev1.Secret{
ObjectMeta: metadata,
Data: map[string][]byte{},
}
if ing.Type == "Opaque" {
serv.Type = corev1.SecretTypeOpaque
value := ing.Opaque.Value
if ing.Opaque.IsBase64 {
// 对值进行base64转码
value = base64.StdEncoding.EncodeToString([]byte(value))
}
fmt.Println(ing.Opaque.Name, value, "===============")
serv.Data[ing.Opaque.Name] = []byte(value)
} else if ing.Type == "docker_registry" {
// 生成docker config json
auth := base64.StdEncoding.EncodeToString([]byte(fmt.Sprintf("%s:%s", ing.DockerRegistry.Username, ing.DockerRegistry.Password)))
authEntry := AuthEntry{
Username: ing.DockerRegistry.Username,
Password: ing.DockerRegistry.Password,
Auth: auth,
}
dockerConfig := DockerConfig{
Auths: map[string]AuthEntry{
ing.DockerRegistry.Repo: authEntry,
},
}
configJSON, err := json.Marshal(dockerConfig)
if err != nil {
return fmt.Errorf("生成配置问问你家失败: %s", err.Error())
}
// 创建 Secret
serv.Type = corev1.SecretTypeDockercfg
serv.Data[corev1.DockerConfigKey] = configJSON
} else if ing.Type == "tls" {
serv.Type = corev1.SecretTypeTLS
serv.Data[corev1.TLSPrivateKeyKey] = []byte(ing.TLSInfo.Key)
serv.Data[corev1.TLSCertKey] = []byte(ing.TLSInfo.Cert)
} else {
return fmt.Errorf("不支持的类型")
}
if _, err := global.K8S.CoreV1().Secrets(ing.Namespace).Create(context.TODO(), serv, metav1.CreateOptions{}); err != nil {
return err
}
return nil
}(2)在 internal/pkg/k8s/secret/delete.go 中创建以下内容,用户删除 secret
package secret
import (
"context"
"github.com/joker-bai/hawkeye/global"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
)
func DeleteSecret(name, namespace string) error {
return global.K8S.CoreV1().Secrets(namespace).Delete(context.TODO(), name, metav1.DeleteOptions{})
}(3)在 internal/pkg/k8s/secret/list.go 中创建以下内容,用于列出 secret 列表
package secret
import (
"context"
"github.com/joker-bai/hawkeye/global"
"github.com/joker-bai/hawkeye/internal/pkg/k8s/dataselect"
corev1 "k8s.io/api/core/v1"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
)
func ListSecret(name, namespace string, page, limit int) ([]corev1.Secret, error) {
global.Log.Info("获取ingress的列表")
list, err := global.K8S.CoreV1().Secrets(namespace).List(context.TODO(), metav1.ListOptions{})
if err != nil {
return nil, err
}
// 做排序
selector := dataselect.DataSelector{
GenericDataList: toCells(list.Items),
DataSelectQuery: &dataselect.DataSelectQuery{
Filter: &dataselect.FilterQuery{
Name: name,
},
Paginate: &dataselect.PaginateQuery{
Limit: limit,
Page: page,
},
},
}
filted := selector.Filter()
data := filted.Sort().Paginate()
return fromCells(data.GenericDataList), nil
}(4)在 internal/pkg/k8s/secret/update.go 中创建以下内容,用于更新 secret
package secret
import (
"context"
"encoding/json"
"github.com/joker-bai/hawkeye/global"
corev1 "k8s.io/api/core/v1"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
)
func UpdateSecret(namespace, content string) error {
var sts corev1.Secret
if err := json.Unmarshal([]byte(content), &sts); err != nil {
return err
}
if _, err := global.K8S.CoreV1().Secrets(namespace).Update(context.TODO(), &sts, metav1.UpdateOptions{}); err != nil {
return err
}
return nil
}(5)在 internal/pkg/k8s/secret/detail.go 中创建以下内容,用于获取 secret 详情
package secret
import (
"context"
"github.com/joker-bai/hawkeye/global"
corev1 "k8s.io/api/core/v1"
metav1 "k8s.io/apimachinery/pkg/apis/meta/v1"
)
func GetSecretDetail(name, namespace string) (*corev1.Secret, error) {
sts, err := global.K8S.CoreV1().Secrets(namespace).Get(context.TODO(), name, metav1.GetOptions{})
if err != nil {
return nil, err
}
return sts, nil
}3、实现 services 方法
3.1、请求参数校验
在 internal/app/requests 目录中新建 k8s_secret.go 文件,写入以下内容以完成请求参数校验:
package requests
import (
"github.com/gin-gonic/gin"
"github.com/joker-bai/hawkeye/pkg/app"
"github.com/thedevsaddam/govalidator"
)
type K8sSecretCreateRequest struct {
Name string `json:"name" form:"name" valid:"name"` // Secret的名字
Namespace string `json:"namespace" form:"namespace" valid:"namespace"` // 名称空间
Description *string `json:"description" form:"description" valid:"description"` // 描述
Labels []Label `json:"labels" form:"labels" valid:"labels"` // 关联标签
Type string `json:"type" form:"type" valid:"type"` // 类型
Opaque Opaque `json:"opaque" valid:"opaque"` // 类型为Opaque的信息
DockerRegistry DockerRegistry `json:"docker_registry" valid:"docker_registry"` // 类型为docker-registry的信息
TLSInfo TLSInfo `json:"tls_info" valid:"tls_info"` // 类型为tls的信息
}
type Opaque struct {
Name string `json:"name" valid:"name"` // 名称
Value string `json:"value" valid:"value"` // 值
IsBase64 bool `json:"is_base64" valid:"is_base64"` // 是否对数据进行Base64编码
}
type DockerRegistry struct {
Repo string `json:"repo" valid:"repo"` // 镜像仓库地址
Username string `json:"username" valid:"username"` // 用户名
Password string `json:"password" valid:"password"` // 密码
}
type TLSInfo struct {
Cert string `json:"cert" valid:"cert"`
Key string `json:"key" valid:"key"`
}
func ValidK8sSecretCreateRequest(data interface{}, ctx *gin.Context) map[string][]string {
rules := govalidator.MapData{
"name": []string{"required"},
"namespace": []string{"required"},
"type": []string{"required"},
}
messages := govalidator.MapData{
"namespace": []string{
"required: namespace不能为空",
},
"name": []string{
"required: name不能为空",
},
"type": []string{
"required: type不能为空",
},
}
return app.ValidateOptions(data, rules, messages)
}
type K8sSecretUpdateRequest struct {
Namespace string `json:"namespace" form:"namespace" valid:"namespace"`
Content string `json:"content" form:"content" valid:"content"`
}
func ValidK8sSecretUpdateRequest(data interface{}, ctx *gin.Context) map[string][]string {
rules := govalidator.MapData{
"namespace": []string{"required"},
"content": []string{"required"},
}
messages := govalidator.MapData{
"namespace": []string{
"required: namespace 不能为空",
},
"content": []string{
"required: content 不能为空",
},
}
// 校验入参
return app.ValidateOptions(data, rules, messages)
}
type K8sSecretListRequest struct {
K8sCommonRequest
Page int `json:"page" form:"page" valid:"page"` // 页数
Limit int `json:"limit" form:"limit" valid:"limit"` // 每页条数
}
func ValidK8sSecretListRequest(data interface{}, ctx *gin.Context) map[string][]string {
rules := govalidator.MapData{
"namespace": []string{"required"},
"page": []string{"required"},
"limit": []string{"required"},
}
messages := govalidator.MapData{
"namespace": []string{
"required: namespace不能为空",
},
"page": []string{
"required: page不能为空",
},
"limit": []string{
"required: limit不能为空",
},
}
// 校验入参
return app.ValidateOptions(data, rules, messages)
}3.2、实现 services 方法
在 internal/app/services/k8s_secret.go 文件中新增 Secret操作的 services 方法,如下:
package services
import (
"github.com/joker-bai/hawkeye/internal/app/requests"
"github.com/joker-bai/hawkeye/internal/pkg/k8s/secret"
corev1 "k8s.io/api/core/v1"
)
// Secret
func (s *Services) K8sSecretList(param *requests.K8sSecretListRequest) ([]corev1.Secret, error) {
return secret.ListSecret(param.Name, param.Namespace, param.Page, param.Limit)
}
func (s *Services) K8sSecretDelete(param *requests.K8sCommonRequest) error {
return secret.DeleteSecret(param.Name, param.Namespace)
}
func (s *Services) K8sSecretUpdate(param *requests.K8sSecretUpdateRequest) error {
return secret.UpdateSecret(param.Namespace, param.Content)
}
func (s *Services) K8sSecretCreate(param *requests.K8sSecretCreateRequest) error {
return secret.CreateSecret(param)
}
func (s *Services) K8sSecretDetail(param *requests.K8sCommonRequest) (*corev1.Secret, error) {
return secret.GetSecretDetail(param.Name, param.Namespace)
}4、新增 controllers 方法
在 internal/app/controllers/api/v1/k8s 目录中新增 secret.go 文件,实现如下方法:
package k8s
import (
"github.com/gin-gonic/gin"
"github.com/joker-bai/hawkeye/global"
"github.com/joker-bai/hawkeye/internal/app/requests"
"github.com/joker-bai/hawkeye/internal/app/services"
"github.com/joker-bai/hawkeye/pkg/app"
"github.com/joker-bai/hawkeye/pkg/errorcode"
"go.uber.org/zap"
)
type SecretController struct{}
// List godoc
// @Summary 列出K8s Secret
// @Description 列出K8s Secret
// @Tags K8s Secret管理
// @Produce json
// @Param name query string false "Secret名" maxlength(100)
// @Param namespace query string false "命名空间" maxlength(100)
// @Param page query int true "页码"
// @Param limit query int true "每页数量"
// @Success 200 {object} string "成功"
// @Failure 400 {object} errorcode.Error "请求错误"
// @Failure 500 {object} errorcode.Error "内部错误"
// @Router /api/v1/k8s/secret/list [get]
func (k *SecretController) List(ctx *gin.Context) {
param := requests.K8sSecretListRequest{}
response := app.NewResponse(ctx)
if ok := app.Validate(ctx, ¶m, requests.ValidK8sSecretListRequest); !ok {
return
}
svc := services.New(ctx)
secrets, err := svc.K8sSecretList(¶m)
if err != nil {
global.Log.Error("获取Secret列表失败", zap.String("error", err.Error()))
response.ToErrorResponse(errorcode.ErrorK8sSecretListFail)
return
}
response.ToResponseList(secrets, len(secrets))
}
// Update godoc
// @Summary 更新Secret
// @Description 更新Secret
// @Tags K8s Secret管理
// @Produce json
// @Param body body requests.K8sSecretUpdateRequest true "body"
// @Success 200 {object} string "成功"
// @Failure 400 {object} errorcode.Error "请求错误"
// @Failure 500 {object} errorcode.Error "内部错误"
// @Router /api/v1/k8s/secret/update [post]
func (k *SecretController) Update(ctx *gin.Context) {
param := requests.K8sSecretUpdateRequest{}
response := app.NewResponse(ctx)
if ok := app.Validate(ctx, ¶m, requests.ValidK8sSecretUpdateRequest); !ok {
return
}
svc := services.New(ctx)
err := svc.K8sSecretUpdate(¶m)
if err != nil {
global.Log.Error("更新Secret失败", zap.String("error", err.Error()))
response.ToErrorResponse(errorcode.ErrorK8sSecretUpdateFail)
return
}
response.ToResponse(gin.H{
"msg": "Secret更新成功",
})
}
// Delete godoc
// @Summary 删除Secret
// @Description 删除Secret
// @Tags K8s Secret管理
// @Produce json
// @Param body body requests.K8sCommonRequest true "body"
// @Success 200 {object} string "成功"
// @Failure 400 {object} errorcode.Error "请求错误"
// @Failure 500 {object} errorcode.Error "内部错误"
// @Router /api/v1/k8s/secret/delete [post]
func (k *SecretController) Delete(ctx *gin.Context) {
param := requests.K8sCommonRequest{}
response := app.NewResponse(ctx)
if ok := app.Validate(ctx, ¶m, requests.ValidK8sCommonRequest); !ok {
return
}
svc := services.New(ctx)
err := svc.K8sSecretDelete(¶m)
if err != nil {
global.Log.Error("删除Secrets失败", zap.String("error", err.Error()))
response.ToErrorResponse(errorcode.ErrorK8sSecretDeleteFail)
return
}
response.ToResponse(gin.H{
"msg": "Secret删除成功",
})
}
// Create godoc
// @Summary 创建Secret
// @Description 创建Secret
// @Tags K8s Secret管理
// @Produce json
// @Param body body requests.K8sSecretCreateRequest true "body"
// @Success 200 {object} string "成功"
// @Failure 400 {object} errorcode.Error "请求错误"
// @Failure 500 {object} errorcode.Error "内部错误"
// @Router /api/v1/k8s/secret/create [post]
func (k *SecretController) Create(ctx *gin.Context) {
param := requests.K8sSecretCreateRequest{}
response := app.NewResponse(ctx)
if ok := app.Validate(ctx, ¶m, requests.ValidK8sSecretCreateRequest); !ok {
return
}
svc := services.New(ctx)
err := svc.K8sSecretCreate(¶m)
if err != nil {
global.Log.Error("创建Secret失败", zap.String("error", err.Error()))
response.ToErrorResponse(errorcode.ErrorK8sSecretCreateFail)
return
}
response.ToResponse(gin.H{
"msg": "Secret创建成功",
})
}
// Detail godoc
// @Summary 获取Secret的详情
// @Description 获取Secret的详情
// @Tags K8s Secret管理
// @Produce json
// @Param name query string false "Secret名" maxlength(100)
// @Param namespace query string false "命名空间" maxlength(100)
// @Success 200 {object} string "成功"
// @Failure 400 {object} errorcode.Error "请求错误"
// @Failure 500 {object} errorcode.Error "内部错误"
// @Router /api/v1/k8s/secret/detail [get]
func (k *SecretController) Detail(ctx *gin.Context) {
param := requests.K8sCommonRequest{}
response := app.NewResponse(ctx)
if ok := app.Validate(ctx, ¶m, requests.ValidK8sCommonRequest); !ok {
return
}
svc := services.New(ctx)
secret, err := svc.K8sSecretDetail(¶m)
if err != nil {
global.Log.Error("获取获取Secret的详情失败", zap.String("error", err.Error()))
response.ToErrorResponse(errorcode.ErrorK8sSecretDetailFail)
return
}
response.ToResponse(gin.H{
"data": secret,
"msg": "获取Secret的详情成功",
})
}再到 pkg/errorcode/k8s.go 文件中新增如下错误代码:
package errorcode
var (
......
// K8s Secret 错误码
ErrorK8sSecretUpdateFail = NewError(500091, "更新K8s Secret 失败")
ErrorK8sSecretDeleteFail = NewError(500092, "删除K8s Secret 失败")
ErrorK8sSecretListFail = NewError(500093, "获取K8s Secret 列表失败")
ErrorK8sSecretDetailFail = NewError(500094, "获取K8s Secret 详情失败")
ErrorK8sSecretCreateFail = NewError(500095, "创建K8s Secret 失败")
)5、新增路由
在 internal/app/routers/k8s.go 文件中新增 Secret操作的路由,如下:
package routers
import (
"github.com/gin-gonic/gin"
v1 "github.com/joker-bai/kubemana/internal/app/controllers/api/v1"
)
type K8sRouter struct{}
func (r *K8sRouter) Inject(router *gin.RouterGroup) {
k8s := router.Group("/k8s")
{
......
// Secret 管理
sec := new(k8s.SecretController)
ks.GET("/secret/list", sec.List)
ks.POST("/secret/create", sec.Create)
ks.POST("/secret/update", sec.Update)
ks.POST("/secret/delete", sec.Delete)
ks.GET("/secret/detail", sec.Detail)
}
}6、测试一下
PS:测试之前都需要先初始化集群,在 4.3.1 Pod 章节有介绍。
这里简单测试列出 Secret 接口,如下:
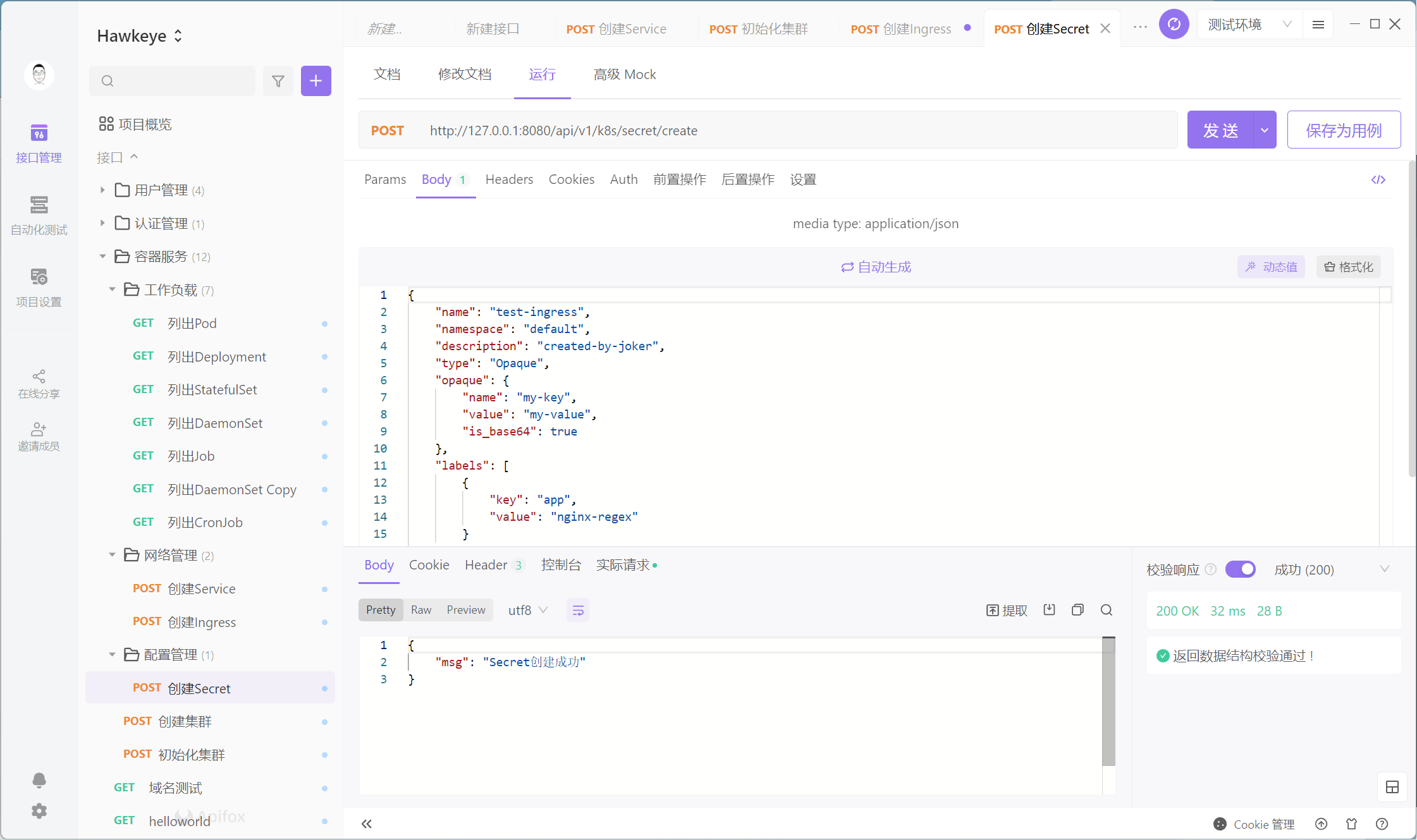
其他接口自行下去测试。
7、代码版本
本节开发完成后,记得生成 swag 和标记代码版本,如下:
$ swag init
$ git add .
$ git commit -m "新增k8s集群secret操作"